Insider Threat Detection with Data Centers
Insider threat detection in data centers is regularly integrating computer-based intelligence and machine learning to monitor and identify suspicious activities across data center infrastructure. Tools such as User and Entity Behavior Analytics (UEBA) by Exabeam and Proofpoint’s Insider Threat Management systems monitor data center operations and data center components to detect abnormal user behaviors. By analyzing data center networking patterns and data center security, these systems flag unauthorized actions, such as data center power consumption anomalies or unexpected data center server access, providing real-time alerts for potential threats.
What is Insider Threat Detection?
Insider Threat Detection provides the process of identifying and managing potential threats from individuals within an organization, for example, employees, who have approved frameworks get authorization to get access to the framework and information. These threats can include malicious actions, such as data theft or sabotage, or unintentional actions, like accidental data sharing. Identification includes checking client conduct, breaking down designs of activity, and using advanced tools. Like machine learning, behavioral analytics, and data loss prevention systems to spot unusual actions that could indicate a security breach or other harmful activities within the organization.
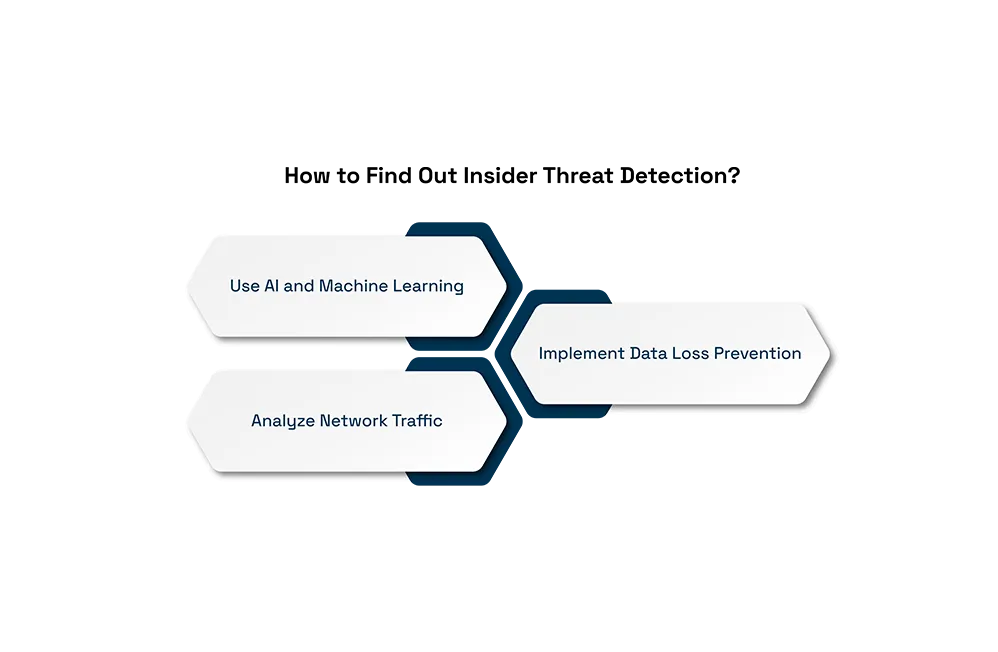
How to Find Out Insider Threat Detection?
- Monitor User Behavior: Track or monitor unusual activities for example abnormal access patterns or data transfers from trusted users within the data center.
- Use AI and Machine Learning: Leverage tools with UEBA (User and Entity Behavior Analytics) to detect anomalies in real time.
- Analyze Network Traffic: Look for irregular network communications or unexpected data flows between servers in the data center.
- Implement Data Loss Prevention: Use DLP frameworks to safeguard unapproved information development or access to delicate data.
- Review Access Logs: consistent audit client access logs for indications of unapproved access or honor abuse.
- Set Up Alerts for Suspicious Activity: Make ongoing alerts for exercises such as large data downloads or access to restricted areas of the data center.
Access Controls and Privilege Management
Access controls and privilege management are hard security measures that ensure only authorized individuals can access sensitive data or systems. By integrating role-based access control, businesses can assign specific permissions based on job roles, minimizing the risk of unauthorized access. Privilege management involves limiting administrative privileges to prevent misuse, ensuring users only have the minimum access necessary to perform their tasks. Regular reviews and updates to access controls help maintain security and protect against insider threats in environments for example data centers.
Tools and Technologies for Insider Threat Detection

Behavioral Data Loss Prevention (DLP)
Behavioral DLP systems focus on monitoring user actions and detecting abnormal behavior that could indicate data theft or accidental data loss. Unlike traditional DLP, which mainly tracks file movements and access behavioral DLP analyzes patterns of user activity over time. If a user starts accessing data they typically don’t work with, transferring large amounts of sensitive data, or violating established policies, the system triggers an alert. This approach helps prevent data leaks and ensures sensitive information remains secure, even if an insider’s behavior changes.
Analyzing Network Traffic for Anomalies
This procedure includes monitoring and analyzing the network traffic within the data center to detect unusual or suspicious operations. By investigating the examples and volume of information moved across networks, it can identify potential insider threats like unauthorized data access or exfiltration. Network anomaly detection tools look for discrepancies in traffic behavior, such as unusual peaks in data volume, communication with unauthorized external IPs, or unexpected ports and protocols. This helps in identifying threats like data breaches or sabotage, often before they escalate.
Unauthorized Access to Sensitive Information
Unauthorized access to important information in data centers offers situations where individuals gain access to confidential data without proper authorization. This can happen within data center infrastructure when employees, contractors, or hackers bypass data center security measures. To mitigate this, data center management must implement strong access controls and privilege management, ensuring only authorized users can access sensitive systems and data. Utilizing data center technologies like data encryption and network traffic analysis further enhances security. Regular data center operations audits and real-time monitoring can help detect and prevent unauthorized access, ensuring the protection of critical data within the data center services environment.